Hey there :)
I talked to a friend the other day, and she was wondering about different types of online communication, what is good and what is bad, what is actually secure ?
So, I'll throw in my random thoughts about the subject here. I would like to point out, this is by no means a do it all, fix it all solution, and no i won't promise you it's stopping that "Three-letter-acronym-agency".
But is it secure "enough", yes I think so. So, if you're curious about secure communications, read on :)
So, let's start with having a look at communication networks, just a overview, so we understand where things can go wrong, where transmission can be intercepted, and how.
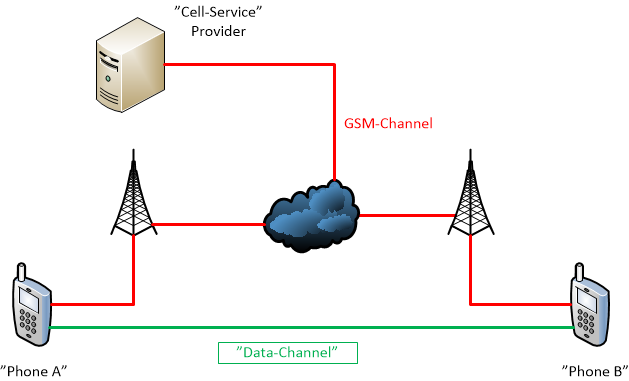
A very simplified GSM network, with a couple of smartphones, Phone A & Phone B.
The red lines, is radio connections running over the public GSM network, so the question comes up, where can these be attacked ?
We could, provided we have a device called a gsm-inteceptor, a fake basestation, see if we could force the phone to connect to that, tell it to drop encryption, and listen in on the call or read texts.
There's only one problem, fake basestations is not very common, they are pretty expensive, and not something you pick up in the local Radioparts-R-US.
The communication channel from cellphone to provider is encrypted, it's an encryption scheme called GSM-A5.2 if I remember correctly. It is considered "good enough" for private / public use. An older version of it, is the GSM-A5.1. That version is not secure, or not as secure as we could hope for, since it can be broken under the right circumstances, and with enough computing power.
And, when it comes down to wiretaps from law enforcement, they usually run a wiretap in your network providers network, where we can't see it. So, how do we protect our privacy ?
Luckily for us, modern phones have data channels, ie internet. So, could we use a VoIP app to handle encryption ?. Sure.
For cellphones, we have Signal IM. It's a pretty nice app, and client. It supports end-to-end encryption, and video/voice and text communications. The good thing about it is that it's paranoid. You need a QR code to pair the desktop client, and you can only pair one extra client at a time, and it doesn't show the messages that were send before the device is paired, so old conversations are hidden.
It also supports timeout on messages, so you can set a delete date / time on them, to clear old messages between you and others. The only thing is, it doesn't use usernames, it uses the cellphone number as a user account. So if you don't want anyone to know you're running Signal IM, get a prepaid card.
So, all in all, a good feature set for an App, and several institutions use it, so I guess it's also good enough for everyday use. For more on that see this link. european-commission-signal-encrypted-messaging.
And, since it's an VoIP app, that doesn't run on the providers gsm channel, it also hides our conversations from them, and everybody else, and for true anonymity, run it from a public network :)
As far as I know, the only thing that could be done to stop it, from a providers point of view, is to drop the data channel, but that would stop Signal from running, so you would know someone is up to no good, and can act accordingly, or find some other way.
If you want to know more about signal foundation and the messenger, stop by here https://signalfoundation.org/
There's also WhatApp, but since it's owned by Facebook, I don't know. Facebook haven't really been the best when it comes to privacy issues. I should point out that WhatsApp is running on the Signal protocol, so it is secure. But, again, since it's Facebook owned, I really don't consider it to be a contender in the sure messenger run.
For the truly paranoid, there's always Tox IM, and TOR. More on that here https://tox.chat/ and here https://www.torproject.org/
That takes care of cellphones, what about messengers ? For that' let's take a look at a network diagram.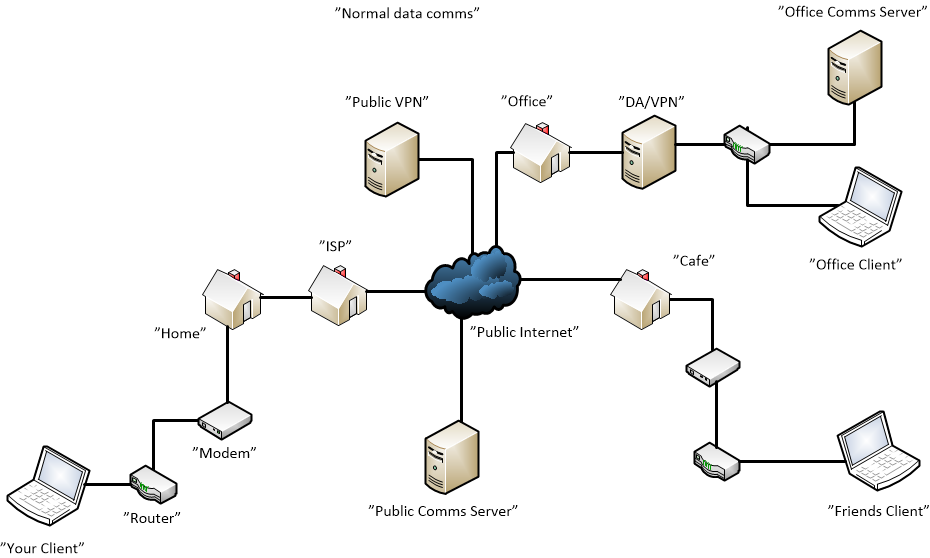
A typical network, including a home, café, "Nosy-ISP.INC", an office, Public VPN provider, a friend, and lastly a public communication server. That last bit could be Facebook, What'App, Signal, A Jabber server, either publicly hosted, or something we run at a hosting provider. The last server called "office comms server" is a special case. It's hosted on our private network, behind af Direct Access Server / VPN. More on that later.
So, what do we have ?. The first attack point is in our own network. Some ARP poisoning from someone sitting in our network with a packet sniffer, and they own us. If it's a connection to a webserver, placed in the public internet, SSL/HTTPS stops that, maybe. There is a technique where you can get the SSL key from the webserver, the Master-Key, and use that to decrypt sniffed packets, but we're not going into that right now, let's keep it simple. And, if we're connected to the "Public Comms Sever", SSL/TLS helps, since our traffic is encrypted in route to the server.
But, let's say we're running SSL/TLS, our "Friends Client" is too. So, now people located in the Café network, and in ours can't see the traffic, unless they can decrypt it with the "Server-Master-Key". So we're good right ?. Well, maybe. What if we can't trust the service provider running the server ?. Here's where it starts to get fun. Enter peer-to-peer encryption. With that, our client software located at "Your Client", and "Friends Client", generate their own keys, use that to generate a session key, and encrypt the conversation. So, with that, we're protected both from Nosy-ISP, and "J Random Hacker", located in our networks.
We can use something like Gajim messenger, https://gajim.org/.
Gajim is running on the Jabber / XMPP protocol. It's an Open Source protocol, and there's a neat little extension, called xep-0384
In plain speak, it's the Omemo encryption extension for XMPP based servers' like prosody.
Prosody is a small and lightweight XMPP server, it's very flexible and easy to handle, and supports a boatload of plugins, so it's worth to have a look at. And, for Android phones, there's an App called conversations, that also support omemo. So, what's good about this. Well, Conversations, Gajim and Prosody, supports peer-to-peer encryption, AND, it also supports encrypted group chats. BUT, the trouble is that it doesn't protect meta-data. So, if someone where to run a packet sniffer on the server, eg "Public Comms Server", they could see meta-data like user IP, usernames, channel data, timestamps and so on. We could of course argue that if we can't trust the server provider, it really doesn't matter, since they have access to the user accounts on the Prosody server, and thus can claim to be our friend, unless we validate who we're talking to each time.
For a list of public XMPP servers' have a look here https://list.jabber.at/
So, can we hide our IP ? sure. Go through the "Public VPN", and get another IP. Use a username that's not directly connected to you, and use a public network, to hide from the VPN provider. Or, simply run from a refurb laptop, paid in cash, and use a prepaid phone card topped up with enough data in your laptop modem. And, while you're at it, use that prepaid phone number to register to Signal IM also.
The trick is that the Signal service only logs connection time, date, and phonenumber. So, using a burner phone aka prepaid card, not a problem. And, use a XMPP server that doesn't keep logs, or if you're running it yourself, turn off logging of connections and conversations.
If you need free public VPN, have a look here https://www.vpngate.net/en/.
But, could we run a Prosody server that is secure ?. We could run it in our office network. If we have a "Direct Access" server running Windows Server, or a Linux VPN server, it helps. Then we control physical access to the server (hopefully), the user accounts, and who got access to it. And since it's running behind a VPN, using SSL, and the clients run omemo peer-to-peer, we are there.
So, there you have it. Some thoughts about protection your privacy in a modern world, what to use and how to use it. But remeber there's no patch for human error.
So, if you're careless with your device, using any kind of identifying data, everyday name, email, phonenunbers and so on, there's really no protection. But then again, it also depends on who you're trying to protect yourself from. If it's "J Random Hacker" or the CIA / NSA.
These app's / programs and advice will protect you from most things, if used right, but as always, think, plan accordingly, and stay alert and practice good computer security routines at all times when these devices are in use. Think about where you use them, how and why, and you should be safe, or at least, safe enough :)


